AES is the industry standard as of now as it allows 128 bit, 192 bit and 256 bit encryption.Symmetric encryption is very fast as compared to asymmetric encryption and are used in systems such as database system. Following is an online tool to generate AES encrypted password and decrypt AES encrypted password. It provides two mode of encryption and decryptio . Ce formulaire vous permet de générer des mots de passe aléatoires. tout d'abord Wpa2 aes password generator vous permet de faire Strong Password Generator pour créer des mots de passe sécurisés Wpa2 aes password generator - Create a secure password using our generator tool
Online Tool for AES Encryption and Decryptio
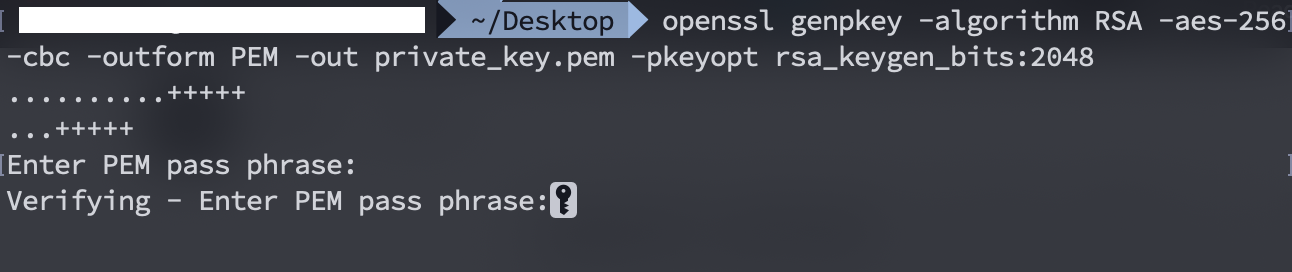
Find out what data encryption is and how it works. Keep your data encrypted and your personal information protected online. Protected keys can be safely stored, transported, and backed up. On the other hand, such keys are inconvenient, because they can not be used without their passphrases. = To generate an RSA key,we will have to use the following genpkey command: $ openssl genpkey -algorithm RSA -out fd.key.pkeyopt rsakeygenbits:2048 -aes-128-cbc.
- A solution I've come up to deal with this so far is to generate a secure key and password hash using AES. Now of course the problem with this is that you still need to secure your keys as they can be used to decrypt your hash into plain text, however the same can be said for PGP or any other reversible encryption
- es its strength. We will explain
- Strong Password Generator to create secure passwords that are impossible to crack on your device without sending them across the Internet, and learn over 30 tricks to keep your passwords, accounts and documents safe
- Use this quick reference guide to help you understand the most common OpenSSL commands.
- Demo of AES encryption in both ECB and CBC mode using OpenSSL toolkit.
Wpa2 aes password generator - Outil en ligne sécurisé
Give our aes256 encrypt/decrypt tool a try! aes256 encrypt or aes256 decrypt any string with just one mouse click Passwords have to be run through a KDF because typical passwords don't contain anywhere near enough entropy to be considered secure against brute force attacks. A KDF substitutes this lack of key space depth with computationally expensive key derivation - hence the thousands of iterations. The disadvantage is the fact that initializing the cipher is also expensive Now that we've covered that part, let's move on to how you can use Powershell to (1) generate and store a 256-bit AES key, (2) encrypt the password for a User Account using that AES key, and (3) use that AES encrypted password in a script (to authenticate with a mail server, in this case). Preparing your environment to use AES encrypted passwords. Use the Powershell below to get your.
Le meilleur générateur de mot de passe en ligne pour créer de bons mots de passe forts, aléatoires, introuvables et sécurisés allant jusqu'à 512 caractères. Gratuit et sans publicité Password Generator: 2,468 sets of passwords generated per day 34,223,905 sets of passwords generated for our visitors : DETECT SECURE CONNECTION INTERCEPTION with GRC's NEW HTTPS fingerprinting service!! Generating long, high-quality random passwords is not simple. So here is some totally random raw material, generated just for YOU, to start with. Every time this page is displayed, our. Every coder needs All Keys Generator in its favorites ! It is provided for free and only supported by ads and donations. GUID; MachineKey; WPA Key; WEP Key; Encryption key; Password; Uppercase ? Yes Braces {} ? Yes Brackets [] ? Yes Hyphens - ? Yes How many ?... Select all Select next Get new results Try our beta version. Framework version . ASP.Net 1.1 ASP.Net 2.0 ASP.Net 4.0 ASP.Net 4.5. How. [ipassword app ] Can lastpass generate passwords With instagram Wpa2 generator or bulk Wpa2 generator ? random password maker As you sign up for accounts, LastPass can generate random passwords for you. When signing up for a new account on a website, click the generate field icon ( ) to open the Wpa2 generator. Select Generate and Fill to use a random password that LastPass automatically generates AES is the industry standard as of now as it allows 128 bit, 192 bit and 256 bit encryption.Symmetric encryption is very fast as compared to asymmetric encryption and are used in systems such as database system. Following is an online tool to generate AES encrypted password and decrypt AES encrypted password. It provides two mode of encryption and decryption ECB and CBC mode. For more info on.
LastPass is free to use as a secure password generator on any computer, phone, or tablet. Anything you create and save on one device is instantly available on the others . The document has moved here Random Password Generator. x Did you like it? Well, then please consider making a donation:) This small site is a result of a hard-working process of one person. Server and domain have been paid with my own funds. All new feature development occasionally happens in the after-work hours only and driven by its owner's desperate passion. If you do like this site or it has helped you by any means.
Create AES secure passwords for use in PowerShell
- Software Downloads for Aes Password Generator There are many examples of 'random' password generator programs on the Internet but many programs do not generate random characters in a way that insures strong security as they use 'built-in' functions that allows to generate pseudorandom numbers. Of course it may be enough randomness for some simple tasks but they can't provide high-quality.
- Aes Password Generator Software Random Password Generator Expert v.2.0 Random Password Generator Expert is a full-featured and powerful, yet small and handy application able to generate passwords of any length and character content
- Insecure Passwords . AES encryption is only as secure as its key. These keys are invariable themselves secured using passwords, and we all know how terrible us humans are at using secure passwords. Keyloggers introduced by viruses, social engineering attacks, and suchlike, can also be effective ways to compromise the passwords which secure AES keys. Use of password managers greatly mitigates.
- In this article, we will share some interesting Linux tips and tricks to generate random passwords and also how to encrypt and decrypt passwords with or without slat method. Security is one of the major concern of digital age. We put on password to computers, email, cloud, phone, documents and what not. We all know the basic to choose the password that is easy to remember and hard to guess.
Secure Password Generator - Packetize
- The next example will add message authentication (using the AES-GCM mode), then will add password to key derivation (AES-256-GCM + Scrypt). Simple AES-CTR Example . Let's start with simple AES-256-CTR non-authenticated encryption. Install Python Libraries pyaes and pbkdf2. First, install the Python library pyaes that implements the AES symmetric key encryption algorithm: Next, install the.
- Password Tech uses strong encryption and hash algorithms such as AES-256, ChaCha20, and SHA-256 to generate random data and protect your data. Individual customization Use a variety of toggles and parameters to customize the passwords and passphrases to your needs
- Password generator. Whenever you need to create a new password, AES Password Manager can automatically generate one that is of high-quality. A high quality password is one that is impossible for others to guess. Lock mode
- Generate 2048-bit AES-256 Encrypted RSA Private Key.pem. The following command will result in an output file of private.pem in which will be a private RSA key in the PEM format. As mentioned in the other answers, previous versions of openssl used a weak key derivation function to derive an AES encryption key from the password. However, openssl v1.1.1 supports a stronger key derivation function.
Right now I think to do this I need to generate a 16-byte salt using a CSPRNG[1]. Than I must prepend the salt with the user password: salt+mypass. Than I must encrypt salt+mypass using AES-CBC which I will use a hardcoded 256 bit key and a randomly generated IV of 16 byte. Effectively I have: AesEncrypt(salt+mypass, GenerateIv(), Key) Given this example, I have a few points which. . However, problem lies within details. The attacker won't need to bruteforce my file with 128bit keys, he bruteforces it with passwords. This is true, 128bit key is often far bigger than what password entropy is. This is why good encryption schemes.
Unser Passwort-Generator ist so konzipiert, dass Sie die einzelnen Elemente frei wählen können. Klicken Sie einfach auf die unterschiedlichen Faktoren und lassen Sie sich ein sicheres Passwort generieren. Zu den einzelnen Punkten sollten folgende Hinweise noch beachtet werden: Groß- und Kleinschreibung. Wenn Sie diese Option bei dem Passwort-Generator einstellen, dann achten Sie bei einem. AES was designed to be efficient in both hardware and software, and supports a block length of 128 bits and key lengths of 128, 192, and 256 bits. How secure is AES encryption algorithm? AES encryption is used by U.S. for securing sensitive but unclassified material, so we can say it is enough secure Useful, free online tool that decrypts AES-encrypted text and strings. No ads, nonsense or garbage, just an AES decrypter. Press button, get result. Features. Pricing. Live API. About Us. Sign In. Sign Up . AES Decryptor web developer and programmer tools. World's simplest AES decryptor. Just paste your text in the form below, enter password, press AES Decrypt button, and you get decrypted.
AES encryption decryption online tool which performs encryption or decryption of an input data based on the given modes (ECB, CBC, CFB or OFB) and key bit sizes (128, 192 or 256 bits) using AES algorithm . Toggle Dropdown. URL Encoder URL Decoder Base64 Encoder/Decoder Bcrypt Hash Generator/Checker AES Encryption/Decryption. JSON Formatter. My Public IP. Developer Tool-kit AES Encryption. AES is the industry standard as of now as it allows 128 bit, 192 bit and 256 bit encryption.Symmetric encryption is very fast as compared to asymmetric encryption and are used in systems such as database system. Following is an online tool to generate AES encrypted password and decrypt AES encrypted password. It provides two mode of encryption. Hashing passwords with a password based key derivation function in .NET | Exercises in .NET with Andras Nemes Once you get the key, you can continue with aes or any other encrption provider using the key you got
The program asks the user for a password (passphrase) for encrypting the data. This passphrase is converted to a hash value before using it as the key for encryption. Curl (Python) Generate Encryption Key Discusses symmetric encryption key generation techniques for block encryption algorithms such as AES, Blowfish,. Hence, AES treats the 128. Using a 256-bit AES key file and a password file. When you use this method you will generate two files: a 256-bit AES key file and a password file. These files can than be used in your PowerShell scripts on local and remote computers. How does this work? The idea is that you create a 256-bit AES key file and one file which contains your.
Strong Random Password Generator
With AES-CBC you usually need a random IV. However, in the case where you use each key only once, like when using password-based encryption with random salts for each file, you can use a fixed, zero IV. So as long as you use a new salt for each file - and even new versions of the same file - you can forgo storing an IV and just use a zero block Jasypt online, free tool for encryption and decryption.This tool supports one way and two way password encryptor using Jasypt as well as matching encrypted password using Jasypt. Programming Testing AI Devops Data Science Design Blog Crypto Tools Dev Feed Login Story. Follow @devglan. Jasypt Online Encryption and Decryption(Free) Jasypt stands for Java Simplified Encryption.It provides basic. Generate random 64/128/158/256bit WEP or 160/504bit WPA key in ASCII or HEX. Provide your ASCII or HEX key - password and automatically find the HEX or ASCII equivalent. Useful for Cisco Access Point encryption configuration Next, generate a random 256-bit initial vector (IV) for the AES CTR block mode and perform the AES-256-CTR encryption: AES encryption of text by text password. We shall use the authenticated encryption construction AES-256-GCM, combined with Scrypt key derivation: from Crypto. Cipher import AES. import scrypt, os, binascii def encrypt_AES_GCM (msg, password): kdfSalt = os. urandom (16. hash generator aes 256 free download. KeePass KeePass Password Safe is a free, open source, lightweight, and easy-to-use password manager for Win
The process for encrypting and decrypting using AES is a bit involved. First you generate an IV (initialization vector) and then generate (or load) a secret key. Next you create a cipher object which you can use for encryption and decryption. Greenhorn. posted 11 years ago. 1; I have written a below program to encrypt a file with AES 128 algorithm. This code works fine. It does encrypt and. A part of the algorithams in the list. Here I am choosing -aes-26-cbc. Symmetric key encryption is performed using the enc operation of OpenSSL.. 1.We can specify the password while giving comman
Bitbucket Generate Ssh Key To Push With Out Password Generate Machine Key Asp Net 4.5 Online Guitar Pro 6 Serial Key Generator Starcraft 2 Collector Edition Key Generator Free Random Aes Key Generator Online Fifa 16 Cd Key Generator Free Download Warcraft 3 Cd Key Generator Generate Public Key From Private Mobaxter Aes Password Generator software, free downloads. Aes Password Generator shareware, freeware, demos: My Password Generator by My Password Generatorcom, X-Lizard Password Generator by Softkhoz Studio, Secure Password Generator by Password Protect Software etc.. For truly random passwords, you can't go past Random Password Generator. The only questions it will ask you are: how many characters do you want (from 6-24) and how many passwords do you want generated? It won't use characters that look similar to each other. E.g. I and 1. Then you hit the search button and up to 100 passwords will be generated for you in that one click. Website: www. Additionally, when AES password encryption is used in a replicated network, if all servers are configured with the same AES passphrase and salt, password data will be replicated in its encrypted form, better protecting the password data. If a server does not support AES, or is configured with different AES information, passwords will be decrypted and replicated as clear text. Note: AES is not.
aes256 encrypt & decrypt online encode-decode
- X5ytd0GuVWI3ZYHfUNO!PkDwi#p%z&sb1EljhaS/M2BnTKReLmo-49,vJqx6+g. Download keys Generate a new encryption keys. Read: Security & Insecurity in pre-shared key mod
- The password is used to generate an AES key which is used to encrypt the file contents. The output file is generated by concatenating the salt, the initialization vector and the encrypted data. It can be decrypted using just the password. See Also. Author Jay Sridhar Posted on November 7, 2017 February 8, 2018 Categories Java Tags crypto, java. Leave a Reply Cancel reply. Your email address.
- Generate secure password in Linux with these tools. Most of the password generation tool discussed here are command line tools. Don't worry, I have not forgotten readers who prefer GUI. This list of password generators for Linux covers both kinds of tools. 1. Pwgen. Now while making truly random passwords is easy if you have the right tools, remembering them is hard. For e.g. my goto tool to.
- Shogun 2 Total War Steam Key GeneratorAes 32 Byte Key Generator Grand Theft Auto 4 Key Generator Free Download -byte salt. 2) Create a 32-byte secret key. 3) Using PBKDF2-HMAC-SHA512 with 100,000 iterations, create a key using the password and the salt. 4) XOR the key and the secret key to create the key to be used to encrypt using AES-256. Represents the abstract base class from which.
- Generate an AES key plus Initialization vector (iv) with openssl and; how to encode/decode a file with the generated key/iv pair; Note: AES is a symmetric-key algorithm which means it uses the same key during encryption/decryption. Generating key/iv pair. We want to generate a 256-bit key and use Cipher Block Chaining (CBC). The basic command to use is openssl enc plus some options:-P.
- SoftFuse Password Generator Free is a freeware program for generating random passwords with ease. Using this program, you can quickly create new password. Generate random passwords, PIN-codes, etc. Protect you information more securely than usually
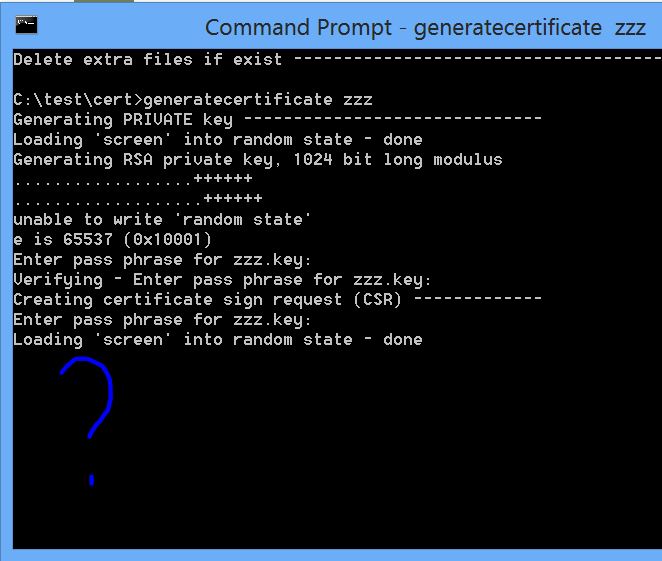
Openssl Generate Aes Key Without Passphrase
Clicking the Generate button will present five passwords for you to select from. Click the Generate button again for further selections. Using this tool is subject to the documents listed within the Legal section. The generated passwords are obviously not stored or otherwise recorded so make sure you remember the one you select to use. Generate strong passwords using secure technology with built-in randomness; Are integrated into a password manager like Dashlane to create, manage, and easily use all of your strong passwords; Learn more. What's a strong password anyway? Long: The longer a password, the more secure it is. A strong password should be at least 12 characters long. Random: Strong passwords use a combination of. The libraries of such coding languages like Java, Python, and C++ implement AES encryption. Password managers. These are the programs that carry a lot of sensitive information. That's why password managers like LastPass and Dashlane don't skip the important step of AES implementation. Even though this is an impressive list of what AES encryption is useful for, it still doesn't include.
security - Create a strong password for AES - Stack Overflo
Learn to use Java AES 256 bit encryption to create secure passwords, and decryption for password validation. To read simple AES encryption, read linked post.. 1. AES - Advanced Encryption Standard. AES is a symmetric encryption algorithm.It was intended to be easy to implement in hardware and software, as well as in restricted environments and offer good defenses against various attack. The password used to generate the SecretKey should be kept in a secure place and not be shared. The salt is used to prevent dictionary attacks against the key in the event your encrypted data is compromised. A 16-byte random initialization vector is also applied so each encrypted message is unique. A look at the internals reveals a structure similar to erickson's answer. As noted in the. Generate Aes Key From Password Microsoft Office 2003 Product Key Generator And Activator Entity Framework Core Generated Key Add Windows 8.1 Oem Product Key Generator C Generate Tripledes Key And Iv Openssl Generate Aes Key From Passphrase Football Manager 2017 Steam Key Generator Indigo Renderer Licence Key Generator Head there and beware of the three tripwires (all which you can disarm to. AESCrypt - AES 128 / AES 192 / AES 256 Class for ASP.NET C# with advanced settings Yet Another AES-Rijndael cryptographic class for ASP.NET C# to easily handle basic and advanced crypto tasks using 128, 192 and 256 Key Length and a whole lot of custom options & settings: Hash, Padding Mode, Cipher Mode, Salt, IV & mor
Video: AES encrypted credentials for Powershell scripts (and a
Generate Aes Key From Password C Kaspersky Antivirus Serial Key Generator V1.1 Adobe Illustrator Cs3 Key Generator Nero 2016 Platinum Serial Key Generator Generate A Pair Of Rsa Keys Microsoft Office Visio Professional 2007 Product Key Generator Nfs Hot Pursuit Key Generator RandomKeygen is a free mobile-friendly tool that offers randomly generated keys and passwords you can use to secure any application, service or device. KEY. RandomKeygen - The Secure Password & Keygen Generator. Menu. More Developer Tools More Developer Tools. JSCompress The JavaScript Compression Tool; DNS-Lookup The Professional DNS & IP Lookup Tool; JSONLint The Legendary JSON Validator. The Java KeyGenerator class (javax.crypto.KeyGenerator) is used to generate symmetric encryption keys.A symmetric encryption key is a key that is used for both encryption and decryption of data, by a symmetric encryption algorithm. In this Java KeyGenerator tutorial I will show you how to generate symmetric encryption keys 2. Once you have typed your password, it will generate your private key. Generating a CSR Request for SSL Certificate. 3. To generate a CSR Request we type the following to generate a request from the private key. # openssl req -out domain.csr -key domain.key -new. 4. Enter the passphrase that you created for the key. 5. Enter Country Name (2.
AES encryption only supports 128-bit (16 bytes), 192-bit (24 bytes) or 256-bit key (32 bytes) lengths, so we'll need to create or generate an appropriate key. For simplicity, let's create a simple byte array of ascending numbers. We'll use a 128-bit key, so we'll need a 16-byte array Sometimes you might need to generate multiple keys. In this situation, When the preceding code is executed, a key and IV are generated when the new instance of Aes is made. Another key and IV are created when the GenerateKey and GenerateIV methods are called. Asymmetric Keys .NET provides the RSA class for asymmetric encryption. This class creates a public/private key pair when you use the.
Générateur De Mot De Passe En Ligne Aléatoire Et Sécuris�
To convert a password to an AES key, PBKDF2 is the simplest way of handling it. Just make the sure the password has sufficient entropy. You do need to use a salt, because it's there to protect against rainbow table attacks. Depending on your platform, there may already be libraries available to help with this. If not, I'd recommend something close to Lucus Kaufman's solution. Setup: Generate a. Intuitif, Wi-Fi Password Key Generator se présente sous la forme d'une simple fenêtre dans laquelle vous renseignez les informations nécessaires à la création d'un mot de passe sécurisé. [System.Runtime.Versioning.UnsupportedOSPlatform(browser)] public abstract class Aes : System.Security.Cryptography.SymmetricAlgorithm The following example demonstrates how to encrypt and decrypt sample data by using the Aes class. using System; using System.IO; using System.Security.Cryptography. WiFi Password Key Generator est un outil de bureau gratuit qui permet de créer rapidement des clés sécurisées WEP / WPA / WPA2 sans fil. Selon l'éditeur: La plupart des périphériques (modems / routeurs) nécessitent la saisie de clés WEP / WPA lors de la configuration de la sécurité sans fil I already know the recommendations about the password, because bad passwords are the weakness of encryption. I also know that the 256bit AES is very safe, but usually it depends from the implementation of that algorithm, this is why I choose GPG rather than 7Zip, it is probably more specialized on encryption
GRC Ultra High Security Password Generator
VeraCrypt is free open-source disk encryption software for Windows, Mac OS X and Linux. In case an attacker forces you to reveal the password, VeraCrypt provides plausible deniability. In contrast to file encryption, data encryption performed by VeraCrypt is real-time (on-the-fly), automatic, transparent, needs very little memory, and does not involve temporary unencrypted files Versions WPA. The Wi-Fi Alliance intended WPA as an intermediate measure to take the place of WEP pending the availability of the full IEEE 802.11i standard. WPA could be implemented through firmware upgrades on wireless network interface cards designed for WEP that began shipping as far back as 1999. However, since the changes required in the wireless access points (APs) were more extensive.

Encryption Key Generator
AES is the industry standard as of now as it allows 128 bit, 192 bit and 256 bit encryption.Symmetric encryption is very fast as compared to asymmetric encryption and are used in systems such as database system. Following is an online tool to generate AES encrypted password and decrypt AES encrypted password. It provides two mode of encryption and decryption ECB and CBC mode. For more info on AES encryption visit this explanation on AES Encryption Password Generator: 2,618 sets of passwords generated per day 33,542,937 sets of passwords generated for our visitors : Sep 13, 2018 The generated key - a Pairwise Master key (PMK) - is used to encrypt data using TKIP/CCMP. The PMK is based on a known value (the passphrase), so anyone with that value (including an employee who leaves the company) could capture the key and potentially use.
RandomKeygen is a free mobile-friendly tool that offers randomly generated keys and passwords you can use to secure any application, service or device. KEY RandomKeygen - The Secure Password & Keygen Generator. With AES-CBC you usually need a random IV. However, in the case where you use each key only once, like when using password-based encryption with random salts for each file, you can use a fixed, zero IV. So as long as you use a new salt for each file - and even new versions of the. 7z (when the password option is used) uses a 256bit AES encryption (with SHA256 key stretching). Install it (p7zip-full), right click on a file or directory you want to encrypt, and choose Compress,.7z and Other options /Password. For decryption, right click on the.7z file and choose Extract here And that is all there is to encrypting and decrypting a file using AES in python. We need to generate or obtain a key, create the initialization vector and write the original file size followed by the IV into the output file. This is followed by the encrypted data. Finally decryption does the same process in reverse. Need to encrypt some text with a password or private key in Python? You. . Asymmetric . RSA Key Generator Diffie-Hellman Key Exchange. Hashing . String Hash Calculator String HMAC Calculator One-Time Password Calculator. Other . Base64 Converter Bitcoin Address Generator. RSA Key Generator. You may generate an RSA private key with the help of this tool. Additionally, it will display the public key of a generated or pasted private. A part of the algorithams in the list. Here I am choosing -aes-26-cbc. Symmetric key encryption is performed using the enc operation of OpenSSL.. 1.We can specify the password while giving comman
WPA PSK (Raw Key) Generator. The Wireshark WPA Pre-shared Key Generator provides an easy way to convert a WPA passphrase and SSID to the 256-bit pre-shared (raw) key used for key derivation. Directions: Type or paste in your WPA passphrase and SSID below. Wait a while. The PSK will be calculated by your browser. Javascript isn't known for its blistering crypto speed. None of this information. AES Advanced Encryption Standard Key sizes 128, 192 or 256 bits Block sizes 128 bits Rounds 10, 12 or 14 Ciphers. AES/CBC/NOPADDING AES 128 bit Encryption in CBC Mode (Counter Block Mode ) PKCS5 Padding AES/CBC/PKCS5PADDING AES 128 bit Encryption in ECB Mode (Electronic Code Book Mode ) No Padding AES/ECB/NOPADDING- AES 128 bit Encryption in ECB Mode (Electronic Code Book Mode ) No Padding AES. Generate a passphrase or test your password's strength (we don't store or transmit these): Approximate Crack Time: 0 seconds The password strength algorithm uses zxcvbn.js, which was created by Dropboxer Dan Wheeler. Site created by @mikehearn. Legal & Tech: The algorithm assumes 10,000 guesses per second, which is consistent with passwords hashed using bcrypt, scrypt or PBKDF2. If a. AES-256 is a solid symmetric cipher that is commonly used to encrypt data for oneself. In In Need to encrypt some text with a password or private key in Python . These are the top rated real world C++ (Cpp) examples of generate_aes_key extracted from open source projects. You can rate examples to help us improve the quality of examples
Wpa2 generator - Strong Secure - Password Generator
AES+CBC encryption require a minimum length of 16 bytes (128bits), AES+GCM can work with 12bytes but 16bytes is recommended. So far so good. W e want to encrypt something, we just generate a. 3. AES Password-Based encryption and decryption. For password-based encryption, we can use the Password-Based Cryptography Specification (PKCS), defined RFC 8018, to generate a key from a given password. For PKCS inputs: Password, you provide this. Salt - At least 64 bits (8 bytes) random bytes Notes on encrypt() function Nonce: A random nonce (arbitrary value) must be a random and unique value for each time our encryption function is used with the same key.Think of it as a random salt for a cipher. The library supplies us with a secure nonce. Scrypt: Scrypt is used to generate a secure private key from the password.This will make it harder for an attacker to brute-force our encryption
Aes 256 Key Generator Online - mybesttre
They make use of a hardware-based set of security modules and an AES engine. When the host writes data to the flash storage device, a Random Number Generator (RNG) generates the 256-bit symmetric cipher key, which is passed to the AES engine. The AES engine encrypts the plain text (source data) into cipher text (encrypted data) and sends it to. Generate the SHA256 hash of any string. This online tool allows you to generate the SHA256 hash of any string. SHA256 is designed by NSA, it's more reliable than SHA1 AES encryption is only as secure as its key. These keys are invariable themselves secured using passwords, and we all know how terrible us humans are at using secure passwords. Keyloggers introduced by viruses, social engineering attacks, and suchlike, can also be effective ways to compromise the passwords which secure AES keys
Password Generator LastPas
public CombinedCipherOutputStream(OutputStream out, Cipher asym, String algorithm) throws IOException, GeneralSecurityException { super (out); // create a new symmetric cipher key used for this stream String keyAlgorithm = getKeyAlgorithm(algorithm); SecretKey symKey = KeyGenerator. getInstance (keyAlgorithm). generateKey (); // place the symmetric key by encrypting it with asymmetric cipher. ENCRYPT PASSWORD password algorithm ENCRYPTKEY {key_name | DEFAULT} . Where: password is the clear-text password. Do not enclose the password within quotes. If the password is case-sensitive, type it that way. algorithm specifies the encryption algorithm to use:. AES128 uses the AES-128 cipher, which has a key size of 128 bits.. AES192 uses the AES-192 cipher, which has a key size of 192. If you want to use the same password for both encryption of plaintext and decryption of ciphertext, then you have to use a method that is known as symmetric-key algorithm. From this article you'll learn how to encrypt and decrypt files and messages with a password from the Linux command line, using OpenSSL. HowTo: Encrypt a File $ openssl enc -aes-256-cbc -salt -in file.txt -out file.txt.enc.
Graviness.co
Openssl Generate Aes Key Without Passphrase Download
Wi-Fi Passwords. WPA2-AES (the same as WPA2-CCMP) can still offer poor security if the password is too short. Nothing can be done to prevent an attacker from capturing network traffic and using a brute force attack to decrypt it off-line, making billions of guesses a second. Just how many billions of guesses per second? According to Paul Moore Passwords: Using 3 Random Words Is A Really Bad. Use PBKDF2 to generate a 256-bit key from your password and the salt, then split that into two 128. And use k2 as your AES key and k3 to verify it. You may also find it useful to generate another key for HMAC, so you can verify that the. Ways to generate symmetric and asymmetric keys. Openssl rand 16 myaes.key AES-256 expects a key of 256 bit, 32 byte. To generate such a key. Run | How To Use. As an MSP, managing passwords in PowerShell scripts can be a dicey task. There is always a risk that someone may find the password by simply taking a peak at your code. However, there are certain scenarios that call for storing a password somewhere and referencing it in a script for authentication. To do this safely you'll need to. Executable freeware AES (256bit)'s interface is just a two field/two button dialog box. One field is for text to encrypt and the other for the password. The two buttons make it easy to encrypt or. Generate random passwords (maximum 100). Each password should be characters long (minimum 6, maximum 24). The passwords will not contain characters or digits that are easily mistaken for each other, e.g., '1' (the digit one) and 'l' (lowercase L). Part 2: Go! Be patient! It may take a little while to generate your passwords..
AES_RNG. The AES_RNG generator uses AES-256, and it will be strong enough to meet most needs as long as its used correctly. It also allows you to use an arbitrarily sized seed because it relies upon SHA-512 to expand then extract entropy that is used to key the underlying cipher The program asks the user for a password (passphrase) for encrypting the data. This passphrase is converted to a hash value before using it as the key for encryption. The following program encrypts a sample text and then prints both the encrypted message and decrypted message on the console. # AES 256 encryption/decryption using pycrypto library import base64 import hashlib from Crypto.Cipher. AES-CTR DRBG is often used as a random number generator in systems that use AES encryption. ANSI X9.17 standard (Financial Institution Key Management (wholesale)), which has been adopted as a FIPS standard as well. It takes as input a TDEA (keying option 2) key bundle k and (the initial value of) a 64-bit random seed s This page uses the javascript functions built into your web browser to generate a random password for you. If you want to see the code for yourself, find your browser's view-source menu item. Importantly, using javascript, all of the computational work for key generation takes place on your own computer. No-one but you knows what random key you got. It is not sent across the internet and. SHA256 Hash. Online tool for creating SHA256 hash of a string. Generate SHA256 message digest from an arbitrary string using this free online SHA256 hash utility HMAC Generator / Tester Tool. Computes a Hash-based message authentication code (HMAC) using a secret key. A HMAC is a small set of data that helps authenticate the nature of message; it protects the integrity and the authenticity of the message. The secret key is a unique piece of information that is used to compute the HMAC and is known both by the sender and the receiver of the message.